Types of Data and Attackers
Personal Data
Any information about you can be considered to be your data. This personal information can uniquely identify you as an individual. This data includes the pictures and messages that you exchange with your family and friends online. Other information, such as name, social security number, date and place of birth, or mother‘s maiden name, is known by you and used to identify you. Information such as medical, educational, financial, and employment information, can also be used to identify you online.
Your computing devices do not just store your data. Now these devices have become the portal to your data and generate information about you.If you have anything of value, the criminals want it.Your online credentials are valuable. These credentials give the thieves access to your accounts.
Organizational Data
Traditional Data
Corporate data includes personnel information, intellectual properties, and financial data.
Internet of Things and Big Data
With the emergence of the Internet of Things (IoT), there is a lot more data to manage and secure. IoT is a large network of physical objects, such as sensors and equipment that extend beyond the traditional computer network. All these connections, plus the fact that we have expanded storage capacity and storage services through the cloud and virtualization, lead to the exponential growth of data. With the velocity, volume, and variety of data generated by the IoT and the daily operations of business, the confidentiality, integrity and availability of this data is vital to the survival of the organization.
Security Model:
A simple but widely-applicable security model is the CIA triad; standing for Confidentiality, Integrity and Availability; three key principles which should be guaranteed in any kind of secure system. This principle is applicable across the whole subject of Security Analysis, from access to a user’s internet history to security of encrypted data across the internet. If any one of the three can be breached it can have serious consequences to the parties concerned.
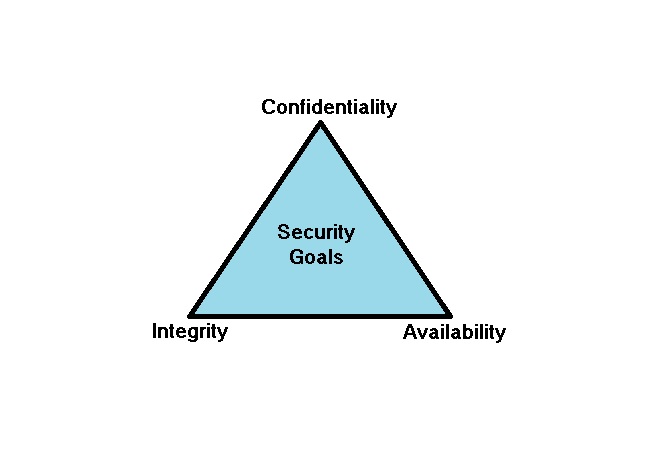
• Confidentiality- Avoiding confidential information from getting leaked to unrelated people.
• Integrity – Avoiding information getting modified without authorization.
• Availability – Availability of information or systems without interruption to people or service.
The Consequences of a Security Breach:
To protect an organization from every possible cyber attack is not feasible, for a few reasons. The expertise necessary to set up and maintain the secure network can be expensive. Attackers will always continue to find new ways to target networks.The monetary cost of a breach is much higher than just replacing any lost or stolen devices, investing in existing security and strengthening the building’s physical security. The company may be responsible for contacting all the affected customers about the breach and may have to be prepared for litigation. With all this turmoil, employees may choose to leave the company. The company may need to focus less on growing and more on repairing its reputation.
Types of Attackers
Attackers are individuals or groups who attempt to exploit vulnerability for personal or financial gain. Attackers are interested in everything, from credit cards to product designs and anything with value.
Hackers and Crackers – The hackers use their knowledge to help security systems and the crackers use their knowledge to break the laws and disrupt security. The two are sometimes called as White Hats and Black Hats. The Hackers being the good guys are called white hats while black hats usually refer to the crackers who violate computer security for personal gains.
Amateurs – These people are sometimes called Script Kiddies. They are usually attackers with little or no skill, often using existing tools or instructions found on the Internet to launch attacks.
Organized Hackers – These hackers include organizations of cyber criminals, hacktivists, terrorists, and state-sponsored hackers. Cyber criminals are usually groups of professional criminals focused on control, power, and wealth. The criminals are highly sophisticated and organized, and they may even provide cyber crime as a service to other criminals. Hacktivists make political statements to create awareness to issues that are important to them.
Internal Security Threats – Attacks can be originated from within an organization or from outside of the organization. An internal user, such as an employee or contract partner, can accidently or intentionally:
- Mishandle confidential data
- Threaten the operations of internal servers or network infrastructure devices
- Facilitate outside attacks by connecting infected USB media into the corporate computer system
- Accidentally invite malware onto the network through malicious email or websites
Internal threats also have the potential to cause greater damage than external threats, because internal users have direct access to the building and its infrastructure devices. Employees also have knowledge of the corporate network, its resources, and its confidential data, as well as different levels of user or administrative privileges.
What is Cyberwarfare?
Cyberspace has become another important dimension of warfare, where nations can carry out conflicts without the clashes of traditional troops and machines. This allows countries with minimal military presence to be as strong as other nations in cyberspace. Cyberwarfare is an Internet-based conflict that involves the penetration of computer systems and networks of other nations. These attackers have the resources and expertise to launch massive Internet-based attacks against other nations to cause damage or disrupt services, such as shutting down a power grid.
The main purpose of cyberwarfare is to gain advantage over adversaries, whether they are nations or competitors.A nation can continuously invade other nation’s infrastructure, steal defense secrets, and gather information about technology to narrow the gaps in its industries and military. Besides industrial and militaristic espionage, cyberwar can sabotage the infrastructure of other nations and cost lives in the targeted nations.
Security Vulnerabilities and Exploitation
Finding Security Vulnerabilities
Security vulnerabilities are any kind of software or hardware defect. After gaining knowledge of a vulnerability, malicious users attempt to exploit it. An exploit is the term used to describe a program written to take advantage of a known vulnerability. The act of using an exploit against a vulnerability is referred to as an attack. The goal of the attack is to gain access to a system, the data it hosts or to a specific resource.
Software vulnerabilities
Software vulnerabilities are usually introduced by errors in the operating system or application code, despite all the effort companies put into finding and patching software vulnerabilities, it is common for new vulnerabilities to surface. Microsoft, Apple, and other operating system producers release patches and updates almost every day. Application updates are also common. Applications such as web browsers, mobile apps and web servers are often updated by the companies or organizations responsible for them.
Hardware vulnerabilities
Hardware vulnerabilities are often introduced by hardware design flaws.Hardware vulnerabilities are specific to device models and are not generally exploited through random compromising attempts.Also any means by which code/software can be introduced to a computer is inherently a hardware vulnerability. Traditional malware protection and a physical security(locked door/cabinet) are sufficient protection for the everyday user.
Categorizing Security Vulnerabilities
Most software security vulnerabilities fall into one of the following categories:
Buffer overflow – This vulnerability occurs when data is written beyond the limits of a buffer. Buffers are memory areas allocated to an application. By changing data beyond the boundaries of a buffer, the application accesses memory allocated to other processes. This can lead to a system crash, data compromise, or provide escalation of privileges.
Non-validated input – Programs often work with data input. This data coming into the program could have malicious content, designed to force the program to behave in an unintended way. Consider a program that receives an image for processing. A malicious user could craft an image file with invalid image dimensions. The maliciously crafted dimensions could force the program to allocate buffers of incorrect and unexpected sizes.
Race conditions – A race condition exists when changes to the order of two or more events can cause a change in behavior. If the correct order of execution is required for the proper functioning of the program, this is a bug. If an attacker can take advantage of the situation to insert malicious code, change a filename, or otherwise interfere with the normal operation of the program, the race condition is a security vulnerability. Attackers can sometimes take advantage of small time gaps in the processing of code to interfere with the sequence of operations, which they then exploit.
Weaknesses in security practices – Systems and sensitive data can be protected through techniques such as authentication, authorization, and encryption.It is strongly advised that developers use security libraries that have already been created, tested, and verified.
Access-control problems – Access control is the process of controlling who does what and ranges from managing physical access to equipment to dictating who has access to a resource, such as a file, and what they can do with it, such as read or change the file. Many security vulnerabilities are created by the improper use of access controls.
Types of Malware
Malware is any code that can be used to steal data, bypass access controls, or cause harm to, or compromise a system. Below are a few common types of malware:
Spyware – This malware is designed to track and spy on the user. Spyware often includes activity trackers, keystroke collection, and data capture.Spyware often bundles itself with legitimate software or with Trojan horses.
Adware – Advertising supported software is designed to automatically deliver advertisements. Adware is often installed with some versions of software. Some adware is designed to only deliver advertisements but it is also common for adware to come with spyware.
Bot – From the word robot, a bot is malware designed to automatically perform action, usually online. While most bots are harmless, one increasing use of malicious bots are botnets. Several computers are infected with bots which are programmed to quietly wait for commands provided by the attacker.
Ransomware – This malware is designed to hold a computer system or the data it contains captive until a payment is made. Ransomware is spread by a downloaded file or some software vulnerability.
Scareware – This is a type of malware designed to persuade the user to take a specific action based on fear. Scareware forges pop-up windows that resemble operating system dialogue windows.The messages typically say that a large number of problems — such as infected files — have been found on the computer and the user is prompted to purchase software to fix the problems. In reality, no problems were detected and the suggested software purchase may actually contain real malware.
Rootkit – This malware is designed to modify the operating system to create a backdoor. Attackers then use the backdoor to access the computer remotely. Most rootkits take advantage of software vulnerabilities to perform privilege escalation and modify system files.Often, a computer infected by a rootkit must be wiped and reinstalled.
Virus – A virus is malicious executable code that is attached to other executable files, often legitimate programs. Most viruses require end-user activation and can activate at a specific time or date. Viruses can be harmless and simply display a picture or they can be destructive, such as those that modify or delete data. Viruses can also be programmed to mutate to avoid detection. Most viruses are now spread by USB drives, optical disks, network shares, or email.
Trojan horse – A Trojan horse is malware that carries out malicious operations under the guise of a desired operation. Often, Trojans are found in image files, audio files or games. A Trojan horse differs from a virus because it binds itself to non-executable files.
Worms – Worms are malicious code that replicate themselves by independently exploiting vulnerabilities in networks. Worms usually slow down networks. Whereas a virus requires a host program to run, worms can run by themselves.After a host is infected, the worm is able to spread very quickly over the network.Worms are responsible for some of the most devastating attacks on the Internet.
Man-In-The-Middle (MitM) – MitM allows the attacker to take control over a device without the user’s knowledge. With that level of access, the attacker can intercept and capture user information before relaying it to its intended destination.MitM attacks are widely used to steal financial information.
Man-In-The-Mobile (MitMo) – A variation of man-in-middle, MitMo is a type of attack used to take control over a mobile device. When infected, the mobile device can be instructed to exfiltrate user-sensitive information and send it to the attackers.
Methods used to gain unauthorized access
In recent years networks have become more secure through server hardening and deployment of security devices such as firewalls and intrusion prevention systems.As a result, hackers and cyber criminals are increasingly resorting to indirect attacks which are described as follows.
Social Engineering
Social engineering is an access attack that attempts to manipulate individuals into performing actions or divulging confidential information.
These are some types of social engineering attacks:
- Pretexting – This is when an attacker calls an individual and lies to them in an attempt to gain access to privileged data. An example involves an attacker who pretends to need personal or financial data in order to confirm the identity of the recipient.
- Tailgating – This is when an attacker quickly follows an authorized person into a secure location.
- Something for Something (Quid pro quo) – This is when an attacker requests personal information from a party in exchange for something, like a free gift.
Phishing
Phishing is when a malicious party sends a fraudulent email disguised as being from a legitimate, trusted source. The message intent is to trick the recipient into installing malware on their device, or into sharing personal or financial information.
Spear phishing is a highly targeted phishing attack. While phishing and spear phishing both use emails to reach the victims, spear phishing emails are customized to a specific person. The attacker researches the target’s interests before sending the email.
Wi-Fi Password Cracking
Wi-Fi password cracking is the process of discovering the password used to protect a wireless network. These are some techniques used in password cracking:
- Social engineering – The attacker manipulates a person who knows the password into providing it.
- Brute-force attacks – The attacker tries several possible passwords in an attempt to guess the password.
- Network sniffing – By listening and capturing packets sent on the network, an attacker may be able to discover the password if the password is being sent unencrypted.
Vulnerability Exploitation
Exploiting vulnerabilities is another common method of infiltration. Attackers will scan computers to gain information about them.
Advanced Persistent Threats
One way in which infiltration is achieved is through advanced persistent threats (APTs). They consist of a multi-phase, long term, stealthy and advanced operation against a specific target. Due to its complexity and skill level required, an APT is usually well funded. An APT targets organizations or nations for business or political reasons.

DoS
Denial-of-Service (DoS) attacks are a type of network attack. A DoS attack results in some sort of interruption of network service to users, devices, or applications. ICMP flood is an example of DoS attack.
There are two major types of DoS attacks:
- Overwhelming Quantity of Traffic – This is when a network, host, or application is sent an enormous quantity of data at a rate which it cannot handle. This causes a slowdown in transmission or response, or a crash of a device or service.
- Maliciously Formatted Packets – This is when a maliciously formatted packet is sent to a host or application and the receiver is unable to handle it.
DoS attacks are considered a major risk because they can easily interrupt communication and cause significant loss of time and money. These attacks are relatively simple to conduct, even by an unskilled attacker.
DDoS
A Distributed DoS Attack (DDoS) is similar to a DoS attack but originates from multiple, coordinated sources.
As an example, a DDoS attack could proceed as follows:
An attacker builds a network of infected hosts, called a botnet. The infected hosts are called zombies. The zombies are controlled by handler systems.The zombie computers constantly scan and infect more hosts, creating more zombies. When ready, the hacker instructs handler systems to make the botnet of zombies carry out a DDoS attack. Smurf attack is an example of DDoS attack.
SEO Poisoning
Search engines such as Google work by ranking pages and presenting relevant results based on users’ search queries. Depending on the relevancy of web site content, it may appear higher or lower in the search result list. SEO, short for Search Engine Optimization, is a set of techniques used to improve a website’s ranking by a search engine. While many legitimate companies specialize in optimizing websites to better position them, a malicious user could use SEO to make a malicious website appear higher in search results. This technique is called SEO poisoning.
What is a Blended Attack?
Blended attacks are attacks that use multiple techniques to compromise a target. By using several different attack techniques at once, attackers have malware that are a hybrid of worms, Trojan horses, spyware, keyloggers, spam and phishing schemes. This trend of blended attacks is revealing more complex malware and placing user data at great risk.
What is Impact Reduction?
While the majority of successful companies today are aware of common security issues and put considerable effort towards preventing them, no set of security practices is 100% efficient. Because a breach is likely to happen if the prize is big, companies and organizations must also be prepared to contain the damage.It is important to understand that the impact of a breach is not only related to the technical aspect of it, stolen data, damaged databases, or damage to intellectual property, the damage also extends to the company’s reputation. Responding to a data breach is a very dynamic process.
Conclusion – Risk Triad
In order to plan for IT security the first and foremost thing would be to define the scope of IT Asset to be protected. The IT Asset can be anything like a USB memory or SD Card memory having confidential data. Once the IT Asset is defined the threats w.r.t the IT Asset can be clearly segregated. One of the threat which we can give as an example is a magnet. Here we can expect no risk as long as there are no vulnerabilities even with the existence of threat. On the other hand if there are vulnerabilities and no threat, again this will not result in any risk. An example of vulnerability can be anything like distance between the magnet and storage device.
So we can say that threat combined with vulnerability will result in risk for an IT Asset. The same is depicted in the figure below.
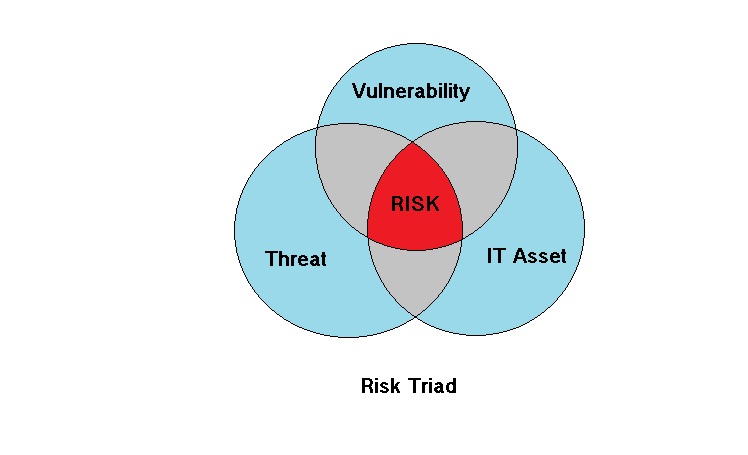
In order to know about securing your data against various threats refer to my blog here. By the way any comments are welcome about the blog.
Sources :
Online Certification on Cybersecurity(www.netacad.com)
情報セキュリテイマネジメント試験 教科書(IT Security Management Test Textbook)
Online Learnings

Leave a Reply