Protecting Data and Privacy
Here the focus will be on protecting devices, creating strong passwords and safely using wireless networks. Also maintaining the data securely will be looked into.
Protect Computing Devices
Your computing devices store your data and are the portal to your online life.
Below is a short list of steps you can take to protect your computing devices from intrusion:
- Keep the Firewall On – Whether it is a software firewall or a hardware firewall on a router, the firewall should be turned on and updated to prevent hackers from accessing your personal or company data.
- Use Antivirus and Antispyware – Antivirus software is designed to scan your computer and incoming email for viruses and delete them. Sometimes antivirus software also includes antispyware. Keep your software up to date to protect your computer from the newest malicious software.
- Manage Your Operating System and Browser – Hackers are always trying to take advantage of vulnerabilities in your operating systems and your web browsers. To protect your computer and your data, set the security settings on your computer and browser at medium or higher. Update your computer’s operating system including your web browsers and regularly download and install the latest software patches and security updates from the vendors.
- Protect All Your Devices – Your computing devices, whether they are PCs, laptops, tablets, or smartphones, should be password protected to prevent unauthorized access. The stored information should be encrypted, especially for sensitive or confidential data.
IoT devices pose an even greater risk than your other computing devices. While desktop, laptop and mobile platforms receive frequent software updates, most of the IoT devices still have their original firmware.If vulnerabilities are found in the firmware, the IoT device is likely to stay vulnerable.The best way to protect yourself from this scenario is to have IoT devices using an isolated network, sharing it only with other IoT devices.
Use Wireless Networks Safely
Wireless networks allow Wi-Fi enabled devices, such as laptops and tablets, to connect to the network by way of the network identifier, known as the Service Set Identifier (SSID). To prevent intruders from entering your home wireless network, the pre-set SSID and default password for the browser-based administrative interface should be changed.Furthermore, you should encrypt wireless communication by enabling wireless security and the WPA2 encryption feature on the wireless router. Even with WPA2 encryption enabled, the wireless network can still be vulnerable.
Use Unique Passwords for Each Online Account or Passphrase
You probably have more than one online account, and each account should have a unique password. That is a lot of passwords to remember. However, the consequence of not using strong and unique passwords leaves you and your data vulnerable to cyber criminals.
To prevent unauthorized physical access to your computing devices, use passphrases, rather than passwords. It is easier to create a long passphrase than a password, because it is generally in the form of a sentence rather than a word. The longer length makes passphrases less vulnerable to dictionary or brute force attacks. Furthermore, a passphrase maybe easier to remember, especially if you are required to change your password frequently.
Encrypting, Back up or Deleting Your Data permanently
Your data should always be encrypted. You may think you have no secrets and nothing to hide so why use encryption? Maybe you think that nobody wants your data. Most likely, this is probably not true.Malicious application infects your computer or mobile device and can steal potentially valuable information, such as account numbers and passwords, and other official documents. That kind of information can lead to identity theft, fraud, or ransom. Criminals may decide to simply encrypt your data and make it unusable until you pay the ransom.
Your hard drive may fail. Your laptop could be lost. Your smart phone stolen. Maybe you erased the original version of an important document. Having a backup may prevent the loss of irreplaceable data, such as family photos. To back up data properly, you will need an additional storage location for the data such as online storage and you must copy the data to that location regularly and automatically.
When you move a file to the recycle bin or trash and delete it permanently, the file is only inaccessible from the operating system. Anyone with the right forensic tools can still recover the file due to a magnetic trace left on the hard drive.To prevent the recovery of deleted files, you may need to use tools specifically designed to do just that like SDelete from Microsoft and Shred for Linux and Secure Empty Trash for Mac OSX.
Different types of Authentication
• Two Factor Authentication
Popular online services, such as Google, Facebook, Twitter, LinkedIn, Apple and Microsoft, use two factor authentication to add an extra layer of security for account logins. Besides the username and password, or personal identification number (PIN) or pattern, two factor authentication requires a second token, such as physical (phone number) or biometric(finger print) authentication.Even with two factor authentication, hackers can still gain access to your online accounts through attacks such as phishing attacks, malware, and social engineering.
• OAuth 2.0
Open Authorization (OAuth) is an open standard protocol that allows an end user’s credentials to access third party applications without exposing the user’s password. OAuth acts as the middle man to decide whether to allow end users access to third party applications. For example, say you want to access web application XYZ, and you do not have a user account for accessing this web application. However, XYZ has the option to allow you to log in using the credentials from a social media website ABC. So you access the website using the social media login.
Ultimately, it is your responsibility to safeguard your data, your identity, and your computing devices. When you send an email, should you include your medical records? The next time you browse the Internet, is your transmission secure? Just a few simple precautions may save you problems later.
Protecting the Organization
Here we cover some of the technology and processes used by cybersecurity professionals when protecting an organization’s network, equipment and data. First, we briefly cover the many types of firewalls, security appliances, and software that are currently used, including best practices.
Next, we will get to know about botnets, the kill chain, behavior-based security, and using NetFlow to monitor a network. The last section discusses about different approaches to cybersecurity, including the CSIRT team and the security playbook.
Firewalls, Security Appliances and best practices
• Firewall Types
A firewall is a wall or partition that is designed to prevent fire from spreading from one part of a building to another. In computer networking, a firewall is designed to control, or filter, which communications are allowed in and which are allowed out of a device or network.
A firewall can be installed on a single computer with the purpose of protecting that one computer (host-based firewall), or it can be a stand-alone network device that protects an entire network of computers and all of the host devices on that network (network-based firewall).
• Port Scanning
Port-scanning is a process of probing a computer, server or other network host for open ports. In networking, each application running on a device is assigned an identifier called a port number. This port number is used on both ends of the transmission so that the right data is passed to the correct application. Port-scanning can be used maliciously as a reconnaissance tool to identify the operating system and services running on a computer or host, or it can be used harmlessly by a network administrator to verify network security policies on the network.
For the purposes of evaluating your own computer network’s firewall and port security, you can use a port-scanning tool like Nmap to find all the open ports on your network. Port-scanning can be seen as a precursor to a network attack and therefore should not be done on public servers on the Internet, or on a company network without permission.
• Security Appliances
Today there is no single security appliance or piece of technology that will solve all network security needs. Because there is a variety of security appliances and tools that need to be implemented, it is important that they all work together. Security appliances are most effective when they are part of a system. Security appliances can be stand-alone devices, like a router or firewall, a card that can be installed into a network device, or a module with its own processor and cached memory. Security appliances can also be software tools that are run on a network device.
Security appliances fall into these general categories:
- Routers – Have many firewall capabilities besides just routing functions, including traffic filtering, the ability to run an Intrusion Prevention System (IPS), encryption, and VPN capabilities for secure encrypted tunneling.
- Firewalls – Capabilities of an ISR router, as well as, advanced network management and analytics.
- IPS – Dedicated to intrusion prevention.
- VPN – Appliances equipped with a Virtual Private Network (VPN) server and client technologies are designed for secure encrypted tunneling.
- Malware/Antivirus – Advanced Malware Protection (AMP) comes in next generation Cisco routers, firewalls, IPS devices, Web and Email Security Appliances and can also be installed as software in host computers.
- Other Security Devices – This category includes web and email security appliances, decryption devices, client access control servers, and security management systems.
• Detecting Attacks in Real Time
Software is not perfect. When a hacker exploits a flaw in a piece of software before the creator can fix it, it is known as a zero-day attack. Due to the sophistication and enormity of zero-day attacks found today, it is becoming common that network attacks will succeed and that a successful defense is now measured in how quickly a network can respond to an attack. The ability to detect attacks as they happen in real-time, as well as stopping the attacks immediately, or within minutes of occurring, is the ideal goal. Unfortunately, many companies and organizations today are unable to detect attacks until days or even months after they have occurred.
- Real Time Scanning from Edge to Endpoint –
Detecting attacks in real time requires actively scanning for attacks using firewall and IDS/IPS network devices. - DDoS Attacks and Real Time Response –
DDoS is one of the biggest attack threats requiring real-time response and detection. DDoS attacks are extremely difficult to defend against because the attacks originate from hundreds, or thousands of zombie hosts, and the attacks appear as legitimate traffic. - Protecting Against Malware –
How do you provide defense against the constant presence of zero-day attacks, as well as advanced persistent threats (APT) that steal data over long periods of time? One solution is to use an enterprise-level advanced malware detection solution that offers real-time malware detection.
Network administrators must constantly monitor the network for signs of malware or behaviors that reveal the presence of an APT.
• Security Best Practices
Many national and professional organizations have published lists of security best practices. The following is a list of some security best practices:
- Perform Risk Assessment – Knowing the value of what you are protecting will help in justifying security expenditures.
- Create a Security Policy – Create a policy that clearly outlines company rules, job duties, and expectations.
- Physical Security Measures – Restrict access to networking closets, server locations, as well as fire suppression.
- Human Resource Security Measures – Employees should be properly researched with background checks.
- Perform and Test Backups – Perform regular backups and test data recovery from backups.
- Maintain Security Patches and Updates – Regularly update server, client, and network device operating systems and programs.
- Employ Access Controls – Configure user roles and privilege levels as well as strong user authentication.
- Regularly Test Incident Response – Employ an incident response team and test emergency response scenarios.
- Implement a Network Monitoring, Analytics and Management Tool – Choose a security monitoring solution that integrates with other technologies.
- Implement Network Security Devices – Use next generation routers, firewalls, and other security appliances.
- Implement a Comprehensive Endpoint Security Solution – Use enterprise level antimalware and antivirus software.
- Educate Users – Educate users and employees in secure procedures.
- Encrypt data – Encrypt all sensitive company data including email.
Botnets, Kill chain and behavior based security
• Botnet
A botnet is a group of bots, connected through the Internet, with the ability to be controlled by a malicious individual or group. A bot computer is typically infected by visiting a website, opening an email attachment, or opening an infected media file. A botnet can have tens of thousands, or even hundreds of thousands of bots. These bots can be activated to distribute malware, launch DDoS attacks, distribute spam email, or execute brute force password attacks. Botnets are typically controlled through a command and control server. Cyber criminals will often rent out Botnets, for a fee, to third parties for nefarious purposes.
• The Kill Chain in Cyberdefense
In cyber security, the Kill Chain is the stages of an information systems attack. Developed by Lockheed Martin as a security framework for incident detection and response, the Cyber Kill Chain is comprised of the following stages:
- Reconnaissance – The attacker gathers information about the target.
- Weaponization – The attacker creates an exploit and malicious payload to send to the target.
- Delivery – The attacker sends the exploit and malicious payload to the target by email or other method.
- Exploitation – The exploit is executed.
- Installation – Malware and backdoors are installed on the target.
- Command and Control – Remote control of the target is gained through a command and control channel or server.
- Action – The attacker performs malicious actions like information theft, or executes additional attacks on other devices from within the network by working through the Kill Chain stages again.
To defend against the Kill Chain, network security defenses are designed around the stages of the Kill Chain.
These are some questions about a company’s security defenses, based on the Cyber Kill Chain:
- What are the attack indicators at each stage of the Kill Chain?
- Which security tools are needed to detect the attack indicators at each of the stages?
- Are there gaps in the company’s ability to detect an attack?
According to Lockheed Martin, understanding the stages of Kill Chain allowed them to put up defensive obstacles, slow down the attack, and ultimately prevent the loss of data.
• Behavior-Based Security
Behavior-based security is a form of threat detection that does not rely on known malicious signatures, but instead uses informational context to detect anomalies in the network. Behavior-based detection involves capturing and analyzing the flow of communication between a user on the local network and a local, or remote destination. These communications, when captured and analyzed, reveal context and patterns of behavior which can be used to detect anomalies. Behavior-based detection can discover the presence of an attack by a change from normal behavior.
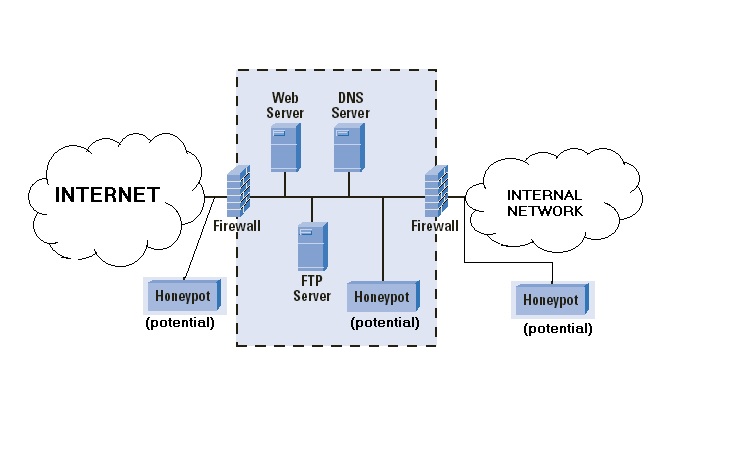
- Honeypots – A Honeypot is a behavior-based detection tool that first lures the attacker in by appealing to the attacker’s predicted pattern of malicious behavior, and then, when inside the honeypot, the network administrator can capture, log, and analyze the attacker’s behavior. This allows an administrator to gain more knowledge and build a better defense.
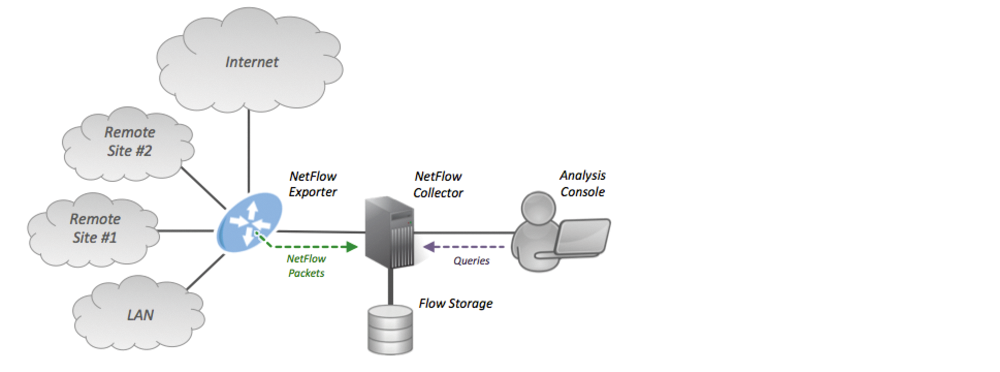
- NetFlow – NetFlow technology is used to gather information about data flowing through a network. NetFlow information can be likened to a phone bill for your network traffic. It shows you who and what devices are in your network, as well as when and how users and devices accessed your network. NetFlow is an important component in behavior- based detection and analysis. Switches, routers, and firewalls equipped with NetFlow can report information about data entering, leaving, and traveling through the network. Information is sent to NetFlow Collectors that collect, store, and analyze NetFlow records.
 CSIRT Team, Security Playbook , Misc
CSIRT Team, Security Playbook , Misc
• CSIRT Team
Many large organizations have a Computer Security Incident Response Team (CSIRT) to receive, review, and respond to computer security incident reports. The primary mission of CSIRT is to help ensure company, system, and data preservation by performing comprehensive investigations into computer security incidents.
There are various types of CSIRTs. An internal CSIRTs is assembled as part of a parent organization, such as a government, a corporation, a university or a research network. National CSIRTs (one type of internal CSIRT), for example, oversee incident handling for an entire country. Typically, internal CSIRTS gather periodically throughout the year for proactive tasks such as DR testing, and on an as-needed basis in the event of a security breach.
• Security Playbook
Technology is constantly changing. That means cyberattacks are evolving too. New vulnerabilities and attack methods are discovered continuously. Security is becoming a significant business concern because of the resulting reputation and financial impact from security breaches. Attacks are targeting critical networks and sensitive data. Organizations should have plans to prepare for, deal with, and recover from a breach.
One of the best way to prepare for a security breach is to prevent one. There should be guidance on identifying the cybersecurity risk to systems, assets, data, and capabilities, protecting the system by the implementation of safeguards and personnel training, and detecting cybersecurity event as soon as possible.
When a security breach is detected, appropriate actions should be taken to minimize its impact and damage. The response plan should be flexible with multiple action options during the breach. After the breach is contained and the compromised systems and services are restored, security measures and processes should be updated to include the lessons learned during the breach.
All this information should be compiled into a security playbook. A security playbook is a collection of repeatable queries (reports) against security event data sources that lead to incident detection and response.Ideally the security playbook must accomplish the following actions:
- Detect malware infected machines.
- Detect suspicious network activity.
- Detect irregular authentication attempts.
- Describe and understand inbound and outbound traffic.
- Provide summary information including trends, statistics, and counts.
- Provide usable and quick access to statistics and metrics.
• IDS and IPS
An Intrusion Detection System (IDS), is either a dedicated network device, or one of several tools in a server or firewall that scans data against a database of rules or attack signatures, looking for malicious traffic. If a match is detected, the IDS will log the detection, and create an alert for a network administrator. The Intrusion Detection System does not take action when a match is detected so it does not prevent attacks from happening. The job of the IDS is merely to detect, log and report.
An Intrusion Prevention System (IPS) has the ability to block or deny traffic based on a positive rule or signature match. One of the most well-known IPS/IDS systems is Snort. The commercial version of Snort is Sourcefire. Sourcefire has the ability to perform real-time traffic and port analysis, logging, content searching and matching, and can detect probes, attacks, and port scans. It also integrates with other third party tools for reporting, performance and log analysis.
• Legal & Ethical Issues in Cybersecurity
Cybersecurity professionals must have the same skills as hackers, especially black hat hackers, in order to protect against attacks. One difference between a hacker and a cybersecurity professional is that the cybersecurity professional must work within legal boundaries.The area of cybersecurity law is much newer than cybersecurity itself. Most countries have some laws in place, and there will be more laws to come.
- Personal Legal Issues
Cybersecurity professionals develop many skills which can be used for good or evil. Those who use their skills within the legal system, to protect infrastructure, networks, and privacy are always in high demand. - Corporate Legal Issues
Most countries have some cybersecurity laws in place. They may have to do with critical infrastructure, networks, and corporate and individual privacy. Businesses are required to abide by these laws.In some cases, if you break cybersecurity laws while doing your job, it is the company that may be punished and you could lose your job. In other cases, you could be prosecuted, fined, and possibly sentenced. - Ethical Issues in Cybersecurity
In addition to working within the confines of the law, cybersecurity professionals must also demonstrate ethical behavior. - Personal Ethical Issues
A person may act unethically and not be subject to prosecution, fines or imprisonment. This is because the action may not have been technically illegal. But that does not mean that the behavior is acceptable. Ethical behavior is fairly easy to ascertain. It is impossible to list all of the various unethical behaviors that can be exhibited by someone with cybersecurity skills. - Below are just two. Ask yourself:
- • Would I want to discover that an IT technician whom I trusted to fix my network, told colleagues personal information gained while working on my network?
- • Would I want to discover that someone has hacked into my computer and altered images in my social network sites?
If your answer to any of these questions was ‘no’, then do not do such things to others. - Corporate Ethical Issues
Ethics are codes of behavior that are sometimes enforced by laws. There are many areas in cybersecurity that are not covered by laws. This means that doing something that is technically legal still may not be the ethical thing to do. Because so many areas of cybersecurity are not (or not yet) covered by laws, many IT professional organizations have created codes of ethics for persons in the industry.Below is a list of three organizations with Codes of Ethics:
• The CyberSecurity Institute (CSI).
• The Information Systems Security Association (ISSA).
• The Association of Information Technology Professionals (AITP).
Sources :
Online Certification on Cybersecurity(www.netacad.com)
情報セキュリテイマネジメント試験 教科書(IT Security Management Test Textbook)
Online Learnings

Leave a Reply